
WordPress has undoubtedly become the platform of choice for both small and large business owners. It powers around 34% of all global websites and 14.7% of the leading websites, which have over 400 million visitors each month. However, because of its immense popularity, it also attracts the attention of hackers and cybercriminals. As a result, over 90,000 hacking attempts are made on WordPress websites every minute!
A security lapse on your website can have far-reaching consequences on your business. Here are just some of the ways a compromised website affects you.
-
SEO ranking: Google and other search engines continually review websites for malware and base SEO rankings according to the health of the site.
- Google blacklisting: Search engines also remove infected sites from search results to keep users from visiting them. This practice is known as blacklisting. They may also place a warning on blacklisted sites in order to protect visitors from malicious content and to prevent them from entering. Not only will this cause your traffic to drop, but even cause existing visitors to leave your site and not return.
- Loss of potential revenue and customers: As mentioned above, blacklist warnings and suspicious behavior of the site will drive existing and potential customers away, which will end up killing your revenues.
-
Damage to brand and reputation: All the goodwill you may have built is ruined, and your brand reputation takes a big hit.
The only way to work around this is to educate yourself and take measures to improve your website’s security posture. Let’s look at five ways in which hackers attack WordPress websites, and follow it up with the five most common WordPress vulnerabilities that cause security problems.
5 Types of Attacks that Can Compromise your WordPress Website
There are many types of hacks that hackers deploy to compromise your WordPress website. Here are the 5 most common online threats to be wary of in 2019:
Brute force attacks
Caused primarily by login page vulnerabilities, brute force attacks are a “trial-and-error” type of attack. They deploy automated bots to try and guess your login page credentials to force their way into your WordPress account.
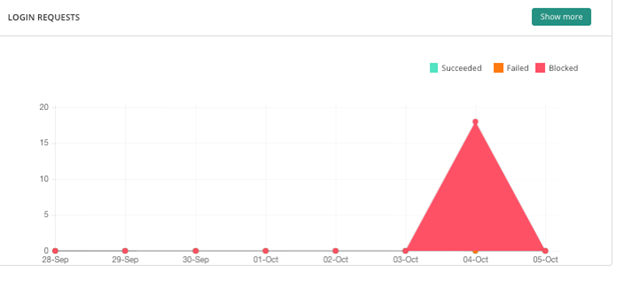
If you haven’t limited the number of failed login attempts, harmful bots keep trying out various username-password combinations on the login page to gain access. A successful brute force attack can seriously compromise your critical website files.
Not just that, even unsuccessful login attempts by such attacks can overload your web server and impact its performance. Additionally, if your website is hosted on a shared web host, your account could be suspended by your web host provider due to system overload.
Cross-Site Scripting
Popularly known as XSS attacks, cross-site scripting is responsible for 84% of all successful hacks on WordPress sites. Here’s how they are executed: The hacker injects insecure JavaScript code on a website through forms that ask for user’s inputs, like the comment section. This loaded script can then be used to steal user data without their knowledge.
SQL Injection
A majority of the WordPress websites use the MySQL database system. SQL injections are a result of malicious code included in queries sent to the MySQL database. When the server containing your database responds to these queries, the hacker gains unauthorized access to your database.
After a successful SQL injection attack, a hacker can create new unauthorized users with “admin” rights or inject malicious links into your MySQL database.
DDoS attacks and Malware
DDoS (or Distributed Denial of Service) attacks target the server with fake web traffic. When used in combination, malware and DDoS attacks can completely wreck and disrupt your website.
While malware attacks are of various types, here are the four most common types:
-
-
Backdoors
-
Drive-by downloads
-
Pharma hacks
-
Malicious redirects
-
File inclusion exploits
Among the common methods used to target WordPress websites, hackers try to gain control of executable PHP files that typically run your WordPress website. For example, wp-config.php is a crucial PHP file in any WordPress installation.
Once they gain access to your PHP file, hackers deploy “file inclusion exploits” to include malicious code that can load and execute remote files, which are used to provide unauthorized website access.
As a WordPress website owner, how can you protect your website from these? You can choose a WordPress security plugin to scan and remove malware and protect against other malicious attacks.
Let’s now look at the 5 most common vulnerabilities that WordPress website owners must guard against.
5 Common WordPress Vulnerabilities that Can Compromise Security
If you’re wondering if WordPress by itself is a vulnerable platform, the answer is no. The core WordPress component is always safe and secure. This is because the WordPress team keeps releasing updates (the latest being version 5.2) that take care of any exploitable security bugs.
So, why do WordPress websites get compromised? Most of them are caused by human error, common oversight, or lack of adherence to safety standards.
-
No timely update of WordPress version and plugins/themes
As a WordPress website owner, you can improve the security of your website by keeping your Core, Plugins, and Themes updated. However, a majority of WordPress websites are currently running on outdated versions, thus making them vulnerable to hackers.
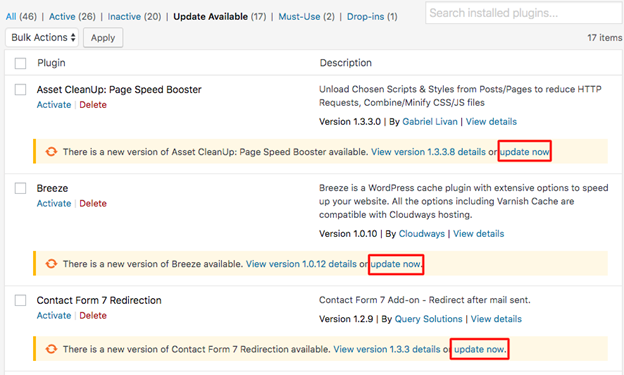
It can be a long and cumbersome task to apply updates to all the installed plugins/themes across multiple websites. You can use tools that offer WordPress management features like a centralized dashboard from where you can manage all plugins/themes.
-
Installing WordPress plugins/themes from Untrustworthy Sources
You can download and install plugins or themes from external websites that could include both trusted and untrusted sources. Those downloaded from trusted sources like the official WordPress Repository are secure. However, plugins/themes from unknown or untrusted sources can have security-related issues that hackers can exploit.
As a safety practice, always download plugins/themes from the WordPress repository or from reliable and trusted WordPress companies and developers.
-
Hosting your WordPress website on unsecured web hosts
Reports show that nearly 41% of hacked websites are a result of poor security measures undertaken by the web hosts. Using an unsecured web host or sharing your web host server with other websites can be a major security issue.
While shared hosting can be a cost-effective solution, it can create major security problems. Even if your hosted website has ample security measures, hackers can gain access to your website through vulnerabilities in the other websites hosted on the same server.
While many web host providers promise you with security for your website, you can never be too sure. As a safety practice, it’s recommended to pick a managed web host that might be more expensive but provides a dedicated server only for your website.
-
Having too many WordPress users with “admin” privileges
Every WordPress website needs an Admin who manages the website, updates plugins/themes, takes website backups, and creates other user accounts. Unfortunately, hackers launch brute force attacks targeting these admin accounts to get access. If successful, they can then inflict maximum damage as only “admin” users would have access to critical website files.
In addition to the “super admin” and “admin” users, WordPress allows you to create other user roles like editor, subscriber, and author, who have lesser privileges.
As a safety practice, restrict the number of “admin” users to reduce the security risk.
-
WordPress websites with no SSL certification
The growth in online banking and payments around the world signifies that more online users are now sharing sensitive information like credit card and banking details through their browsers. Unsecure transfer of such sensitive data can be easily intercepted by hackers and misused.
To secure such transfers, the Secure Socket Layer protocol was devised as a safety measure to encrypt data being transferred between the user’s browser and the webserver. However, a large number of WordPress websites are still not SSL-certified, making them a major security threat. An SSL-certified website is denoted by the https:// sign (or HTTP Secure) preceding the website name, along with the “padlock” sign.
As a safety practice, obtain the SSL certificate from your web host provider or from an external website.
In Conclusion
Through this article, we have presented a complete guide on the ten most common security issues for your WordPress website. This includes five common threats that can compromise your website, along with five common WordPress vulnerabilities and to deal with them. By raising your awareness about the common problems in WordPress security, you are definitely in a better position to ensure your site is protected against hackers.
However, despite all your measures, things could still go wrong. A regular and consistent backup strategy is the first and simplest step to cover your bases. We highly recommend investing in a reliable backup and security service for the peace of mind they guarantee. If you’re looking for a solution that combines the two, check out VaultPress or Malcare.














Great read! Your insights into common WordPress security issues are spot-on. The emphasis on password strength, regular updates, and the use of security plugins is a timely reminder. Thanks for sharing these valuable tips!
Another piece of great and lovely informational content on WordPress security! Thanks for sharing these WordPress security tips. I have thoroughly enjoyed reading this post and would like to read more such enlightening blog posts from your end.
I have been facing some of these issues on my WordPress website and your blog tut. has helped me out on the several ways to fix these issues, thank you.