Spyse is simply a cyberspace search engine, specializing in providing aggregated web data to users. They have recently combined all their products into a single service which greatly simplifies data gathering processes which used to be very long and frustrating in time past.
This cyberspace search engine entirely oversees the processes of data collection and reconnaissance, so that security engineers, pentesters, webmasters, and bug bounty hunters no longer have to perform these tasks manually. Spyse database stores most if not all needed data, enabling specialists to speed up the information gathering process and quickly identify loopholes and vulnerable parts of the internet.
 Read on to learn about Spyse and how it can simplify the workflow of any cybersecurity expert.
Read on to learn about Spyse and how it can simplify the workflow of any cybersecurity expert.
Continuous Data Collection
Spyse employs a unique database approach which makes for instant results on all types of data requests. To make this possible, they utilize a smart system of scanners which parse the internet regularly and collect data.
Specifically, ten scanners are employed to collect data about different technologies and internet objects. These scanners are unique, with each focusing on specific parts of the web, searching for different points of entry, and gathering data from various sources. Before being unleashed to the masses, the data is analyzed by Spyse specialists and interconnected to help users visualize relationships before data.
By having an infrastructure of fifty powerful servers located around the world, Spyse is able to bypass location-based scanning restrictions and ISP blocking. This means that users will always get more data (including a more comprehensive DNS data) with Spyse than they can get anywhere else.
Information Storage
Spyse removes the problem of manually performing scans, which was always the longest process of reconnaissance. Saving time on this is handy, as you can focus on other tasks like patching vulnerabilities or identifying threats, instead of waiting for the scan requests to return.
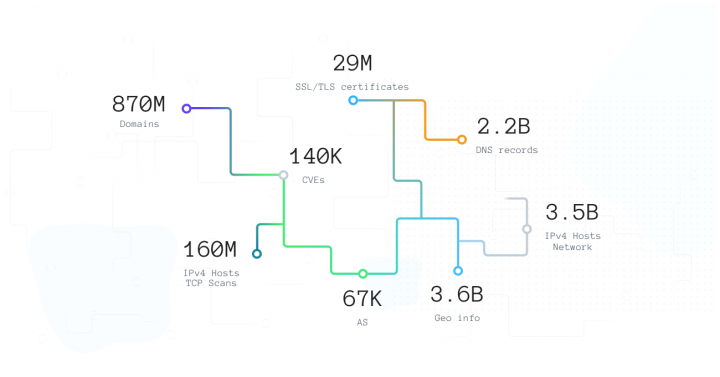
The database itself is composed of fifty highly productive, fast, and expensive servers storing only hot data. This allows Spyse specialists to preview and authenticate the data, before connecting it based on relationships and delivering the full package to the user. Making forty-five terabytes of data and over seven billion documents that are constantly being updated.
How to Extract Data with Spyse (Website & Spyse API)
There are two methods to find and extract data with the Spyse cybersecurity search tool for webmasters and site administrators. The first is the web interface, and then, the API.
The web interface offers aggregated and structured information which is organized into tables. The columns with information found inside these tables can be adjusted and data can be filtered out. Once done collecting data on the website, users can download it for offline storage and access.
Does the web interface feel a bit limited? Users can access the API and integrate it into their services. The API expanded documentation was made with Swagger, which creates lots of flexibility and detail when searching for necessary data.
This API can be easily integrated with your tools and is a great alternative while the team is still working on their CLI. For those staying in trend, check out the Python wrapper made by outsourced developer zer0pwn.
Spyse Productivity Boosting Features
Spyse specializes in speeding up the workflow of security personnel. In addition to the database approach, there are two tools which increase productivity: Advanced Search, and Security Scoring.
The advanced search tool speeds up the process of finding technical data and interesting information tenfold. The main feature of advanced search is the ability to utilize 5 different search parameters in a single query.
With advanced search, using just a few parameters you can find: all live sites (domains with a server response of 200), which belong to a specific company and have certain vulnerabilities on the web platform or technologies/products. This example includes just 3 search parameters, and the possibilities of this search are truly endless.
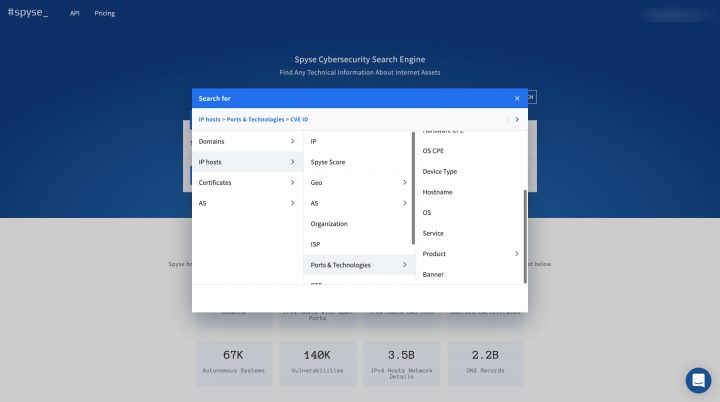
Another instrument in the Spyse arsenal for speeding up workflow is the Security Scoring tool. While advanced search specializes in narrowing down data, Scoring lets you quickly filter a list of targets for finding the most secure or most vulnerable target.
This is extremely useful in bug bounty hunting processes. Scoring takes all the information provided by Spyse scanners, connects it with the CVE and delivers an overall network security rating (numbered from 0-100).
This lets users see the details of every found vulnerability, like CVSS 3.x, and CVSS 2.0, impact, exploitability, attack vectors, references, and many more.
 For Sysadmins, Pentesters, and Bug Bounty Hunters
For Sysadmins, Pentesters, and Bug Bounty Hunters
System administrators can use Spyse to continuously monitor the state of their cyber-infrastructure, by attaining information straight from a ready database (either manually or by writing a few basic scripts). Sysadmins can also analyze security levels of their network or infrastructure and quickly find vulnerabilities and potential entry points that cyber crooks seek to expose.
Pentesters and Bug Bounty Hunters will also find this service a great time and resource saver. As Spyse fully oversees the target information-gathering phase, it can aid in quickly creating a target list and avoid most problems related to information searches.
There’s no need to develop new infrastructures for scanning with Spyse. It helps avoid rate limits and stay invisible while digging for data. Spyse is overall a great OSINT resource to use when others are not allowed by the contract or bounty agreement.
All in all, Spyse saves huge amounts of time and resources for anyone working in cybersecurity by entirely overseeing the process of reconnaissance.
 For Sysadmins, Pentesters, and Bug Bounty Hunters
For Sysadmins, Pentesters, and Bug Bounty Hunters