The issue of ransomware, malware, viruses and cyber attack is not new to the tech world as many deadly viruses has been distributed in the past. In fact, railer odinga virus wrecked some machines as far back as 2000s when the internet of things was still new to a lot of PC users.
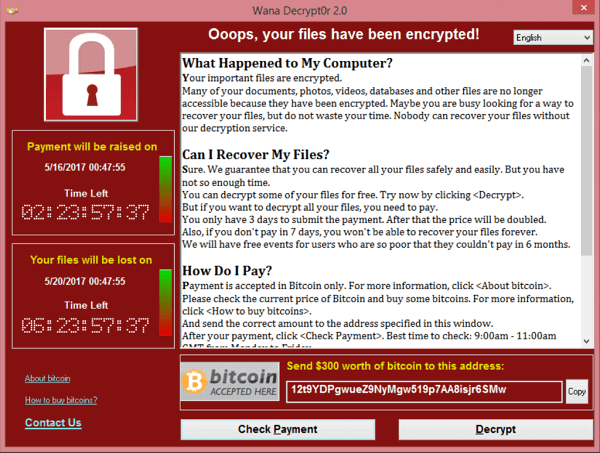
The much-publicized WannaCry ransomware cyber attack that started mid-May and affected over 200,000 personal computers (and networks) in over 150 nations using older Microsoft Windows operating system was our wake-up call to start sensitizing our readers on PC security/safe practices.
We’ve written much about security already, including tips on Mobile security, USB disk security, Information security and lots more, but would like to talk about ransomware and/or other malicious programs today.
Ransomware Meaning and Types
Ransomware is a group of virus or system threat that prevents a user from getting access to his files, documents and/or data until a stated amount is paid. It does this by encrypting all usable files into an unreadable file system, demanding that infected users pay a ransom to get their files back.
In most cases, the malicious program issues a threat to permanently destroy the files if the infected user tries to reclaim them by the use of third-party software other than their suggested solution.
The use of extremely advanced techniques and highly secretive digital currency such as Bitcoin for the payment of ransom has led to an increase in the number of extortion ransomware in recent time.
Type/Sources
Ransomware are easily distributed via infected email attachments, infected websites, infected networks and/or external storage devices. Some ransomware such as locker viruses can be distributed via legitimate software by intercepting the traffic at unpopular download sources.
Irrespective of the sources of ransomware, they are usually harmful and one of the worst form of malware or system threats till date.
The major types of ransomware are Locker ransomware, Encryptor ransomware and Master Boot Record (MBR) ransomware. While locker ransomware locks one out from his PC/Mobile devices completely until a ransom is paid, Encryptors denies one access to his documents and files, asking that they pay a fee for the unlock key. Master Boot Record (MBR) ransomware is another form of Locker ransomware that prevents the complete booting of the infected PC until a ransom is paid.
So far, more than 20 variants of ransomware viruses has been distributed; causing panic, lost of money, data compromise and innumerable damages to their victims. Some of the most popular (widely spread) ones are:
- WannaCry (Wannacrypt): Has infected more than 180,000 computers worldwide by targeting older OS versions with unpatched Microsoft Windows vulnerability. Most server/business networks running unpatched Windows version were their biggest victims.
- Cerber Ransomware: Cerber ransomware distribution was so successful that they created more versions of it as soon as a cure is found for the ones distributed earlier. Cerber ransomware went from version 1 to 5 causing damages and data lost to it’s victims.
- DMA Locker: DMA Locker ransomware was as successful as cerber and locky ransomware attacks. Just like cerber ransomware, it went from version 1 to 5 attacking several millions of PC world over.
- KeRanger: Mac devices are generally believed to receive lower volume of targeted cyber attacks as they aren’t as widely used as their Windows counterpart. But KeRanger ransomware was targeted at Apple Macintosh machines. It successfully infected some users asking that ransom be paid via Bitcoin crypto-currency to regain access to their locked files.
- CryptoLocker, CryptoWall, TorrentLocker, Locky, Reveton, NoobCrypt, Fusob, Uiwix, CTB Locker and TeslaCrypt are some other notorious ransomware that did their worse to terrorize the cyberspace.
Ransomware in its early days were targeted at a selected group/professionals, but are now spread as wide as possible to get as much ransom. Many businesses already paid the ransom money without getting an immediate solution, instead the attackers kept demanding for more without a solution in sight.
This is why we’ll like to guide you on the best methods to combat ransomware and targeted cyber attacks by malicious websites and/or cybercriminals.
Combating Ransomware
Studying about ransomware attacks without learning the best methods to combat it would be at best “an effort in futility”. This is because knowledge is power only when application of the same is possible!
Ransomware as a highly sophisticated cyber attack needs to be kept as far away as possible. This is because preventing ransomware attack is better and safer than trying to remove it. So, we’ll talk more about the best preventive methods for ransomware and/or other cyber attacks.
Regular Update is a Must
Apart from ransomware and criminal cyber attacks, updating your machines regularly lets you enjoy all newer features and critical security patches.
Even if for any reason, the automatic update of your Operating System (OS) is turned off, updating the critical security patches would help you stay safe.
Software and browser plugins update is as important as that of operating systems. This is because many malicious ransomware has been successfully distributed via a vulnerable version Adobe flash player and similar browser plugins.
Remember to turn on the automatic virus database engine update features of your internet security software. Disabling the macros function in Microsoft Office programs is a must for every PC that’s connected to the internet.
Embrace File Backup & Transfer of important Files to an External Storage Source
The days of floppy disks and expensive data storage disks is long gone. Most 2TB external storage drives goes for as low as $60 or even half this amount during promo sales. There’s a hardly a sane reason why you shouldn’t embrace file backup in this stage of Tech.
Microsoft one drive gives 15GB of free data storage space, Mega gives a whopping 50GB of FREE data storage space, Copy and Google drive isn’t left out in the mix of free cloud storage services as they also have thousands of generous storage drive allocation for their free and paying customers alike.
In fact, I’ll recommend a periodic backup of your most valuable documents and files to multiple storage locations. This could be cloud storage services or to an external hard disk drive (HDD).
Avoid Shady Websites
Avoiding shady websites, suspicious web apps and unrealistic web/mobile ads is one sure way to keep malicious schemes at bay.
Installing an ad-blocker or an internet security software that prevents suspicious ads is recommended for those that must visit such websites.
Adult websites and websites that distributes serial keys, free premium software patches, torrents, null themes, cracked plugins, pirated movies and etc. are easy sources for cybercriminals to distribute malware/viruses.
Some PPC advertising services with little or no check on their advertisers can also fuel the spread of ransomware. This is because attackers can easily promote such programs and hijack traffic to user’s machine once a website running such advert is visited.
Another proactive measure to avoid visiting infected websites is by examining all links in emails before clicking on them. It doesn’t matter where or who is sending the email to you, cross-checking all links before visiting is a must for every internet user.
When possible, avoid clicking on links or downloading attachments from emails sent by an unknown sender or from those already caught up by your spam/junk mails filter.
Use an Internet Security App
While most home users anti-virus software such as Avast, Avira and AVG does a good job protecting our machines for free, the need of internet security software is inevitable for business and enterprise users.
Avast Free anti-virus program and security suits from Comodo comes with an intelligent threats engine that does so well in fighting internet viruses, but can’t be compared in practice with a paid Kaspersky internet security app.
Using an internet security program (Kaspersky recommended) over the basic anti-virus programs would give you an edge as it comes with such tools as: Rootkit Malware scanner, stealth scanner, real-time web scanner, real-time PC protection, privacy tools and parental control functions.
Rounding Up
Doing all these might seem boring as it takes away the fun and freedom that comes with owning a digital device. But then, there’s the reality of today’s internet.
Doing all these might seem boring as it takes away the fun that comes with PCs. But then, Security is Priceless!
Governments, criminal chains, hacking start-ups and many other groups are sponsoring the spread of such programs as a fraudulent means to crowd-fund their child projects.
In fact, there’s a good check-list and free ransomware protection plan at heimdalsecurity. I’d advice you check that out to see other good tips for preventing ransomware viruses. Read on for tips on combating ransomware on infected machines.
When Infected by a Ransomware

Paying for the ransom is not recommended at all. This is because it encourages the criminals to cause more cyber havoc and there’s no guarantee of getting back your data after paying to their bitcoin wallet.
Here are some expert-recommended tips for those infected with ransomware and/or other malicious viruses.
Do a System Format
Assuming that your data(s) are safely backed up to cloud or other storage sources, doing a full system format is the first step to combating ransomware attacks by preventing it from spreading further.
You can do this by doing a full OS restore using the backup partition that’s shipped with newer windows PCs or by using a bootable Microsoft windows operating system (OS) disks.
Pressing F9, F12, F9 or F8 (depending on the PC brand) function buttons during cold/warm boot is used to call up the system restore feature. You can use this menu to call up the options that aids you do a full system format or OS partition recovery.
Once the format is completed, install an internet security software and restore your files from the data storage sources.
Attempt Free Decryptors
Some old ransomware viruses are still spreading till date. Searching the net with the “ransomware name + version + solution” could yield a positive result.
There’s a free solution and/or free decryption tool for most popular ransomware. Eset, a security company based in North America once released a tool that lets you decrypt your files from Teslacrypt ransomware after the criminal vendors discontinued their onslaught.
Similar free decryption tools has been released for Cerber1 ransomware, Cerber2 ransomware and several others. Most reputable security software vendors such as: Avast, Kaspersky, Symantec, AVG, Trend Micro et al have come up with free tools that helps users decrypt their files for free.
Even though these free solutions works mostly for old ransomware, it is recommended that you search about the ransomware infection type before trying out the premium options below.
Use Data Recovery Apps
Data Recovery Apps can come in handy for getting back your compromised files. Most ransomware viruses first makes a shadow copy of your original files, encrypts it, and then delete the original version(s) of it. Data recovery software would be very useful for saving the day in case of such ransomware attacks.
To use this solution, you’ll need remove the storage drive from the infected PC, connect it to one with an up-to-date internet security program, and then install a premium data recovery app to attempt a full recovery of the deleted files.
Trying to restore the deleted files back to the same hard disk drive (HDD) is not recommended. So, a PC with free storage space or an external storage media would be best for it.
Use Enterprise Solutions
Depending on how delicate your compromised data is, you may wanna opt to enterprise-level services instead. There is Kaspersky total security software , Comodo Advanced Endpoint Security suits, and lots of services tailored to enterprise users.
In my opinion, it is much more saner to pay legitimate companies offering such services than donate same to cybercriminals that’s going to further their malicious activities with it.
Apart from internet security giants such as: Kaspersky, Symantec and Comodo securities offering such services, there are reputable data recovery companies (such as EaseUS, Stellar Phoenix, Wondershare, et al) that are experts in getting back compromised data(s).
Combating Ransomware InfoGraphic
A picture is worth a thousand words if it’s delivering the right message. Here are the pro-tips for fighting ransomware and malicious viruses presented in a single photo.
Please do share with friends and colleagues in all possible platforms to help them stay safe online.

In Summary
Ransomware, just like other harmful computer viruses can be tamed, controlled, removed and/or completely prevented. All you need do is – follow after the preventive tips above.
The best ransomware removal methods discussed above can come in handy to those already infected. Remember to embrace the discussed file backup options for all your important documents, files and pictures.
Have other tips to share on ransomware removal or an advice on fighting PC/Mobile viruses? Please do shaer with us in comments.

















as i havent received a confirmation email… sorry if it is duplicated:
Hi,
there is no privacy, our data is constantly being taken and sold so they can shell products to you…. and they can control you. We are constantly being programmed by media and society. We are bio-machines and we learn by repetition. And that is what media does, repeat and repeat until you recite it like a parrot :)
I downgraded my windows 10 to windows 7.
I use several security systems in windows. Currently:
Avast free anti-virus
Comodo Internet Security Premium 11
Windows 10 Firewall Control
Zemana Anti-malware
AntiMalwareBytes free (on demand)
Ashampoo Privacy Protector
Glary Utilities 5 (its got spyware remover)
ShieldApps Web-cam blocker (instead of disabling web-cam and mic in COMPMGMT.MSC as I used to do)
Toolwiz TimeFreeze (so I can test… also comodo has a system to isolate apps)
Revo Uninstaller Pro (many functions along with app backup)
CCleaner
monitoring software (loads, specific for cpu, ram, network, io…) like sysinternalssuite, YetAnotherProcessMonitor, whireshark,
proper backup and restore solutions…
…
Windows services, stop and change to manual every update, notifier, upgrade…. things that you can create a task for them or just run check for updates manually when you use the software.
Block with firewall internet access unless is necessary, or even better manually unblock when you need to update…
Disconnect the cable (machine switch for laptops wifi) and connect it only when you need it.
Control over the network, wifi… (412bit password, mac protection, wps off, pwd never sent -I use keepass even in the phone and with a usb cable i can type it directly on any computer-, etc)
Use cable (RJ45 ethernet) and switch off your AP’s wifi (i have a remote that switches on and off the wifi APs whenever i need them), use microUSB OTG ethernet adapter for phones, tablets… even a TV stick like Chromecast or Fire
TimeFreeze, Isolation and Virtualization (now i use Oracle’s as I have no pirate software) work very well.
As i can not afford anything nowadays (chronic Lyme and the insurance doesn’t pay, I ate my savings and now I live from borrowed money from my family and i depend on people as i can not take care of myself everyday) i look for free licenses -giveaways- but i download the software from the official site). Be careful with free stuff….
I’ve got a list of DNS servers that i use, being Cloudfare the main ones..
VPN: I use free ones but sadly i can reroute all my traffic through them :( I wish i had unlimited VPN data…
Encrypted communication (telegram…)
Encrypting data that contains sensible info.
I literally don’t have any extensions, add-ons, etc. because obviously all your data goes through them; except for Comodo Dragon (online security pro extension) as the data is being monitored by them anyway…
Same goes with checking every soft you install, go to settings and look for an information collection -or something like that- and uncheck that option.
and of course: removing windows updates…
wusa /uninstall /quiet /norestart /kb:2505438
wusa /uninstall /quiet /norestart /kb:2506928
wusa /uninstall /quiet /norestart /kb:2545698
wusa /uninstall /quiet /norestart /kb:2592687
wusa /uninstall /quiet /norestart /kb:2660075
wusa /uninstall /quiet /norestart /kb:2670838
wusa /uninstall /quiet /norestart /kb:2726535
wusa /uninstall /quiet /norestart /kb:2876229
wusa /uninstall /quiet /norestart /kb:2923545
wusa /uninstall /quiet /norestart /kb:2952664
wusa /uninstall /quiet /norestart /kb:2970228
wusa /uninstall /quiet /norestart /kb:2976978
wusa /uninstall /quiet /norestart /kb:2990214
wusa /uninstall /quiet /norestart /kb:2994023
wusa /uninstall /quiet /norestart /kb:3021917
wusa /uninstall /quiet /norestart /kb:3022345
wusa /uninstall /quiet /norestart /kb:3035583
wusa /uninstall /quiet /norestart /kb:3050265
wusa /uninstall /quiet /norestart /kb:3065987
wusa /uninstall /quiet /norestart /kb:3068708
wusa /uninstall /quiet /norestart /kb:3075249
wusa /uninstall /quiet /norestart /kb:3080149
–> So.. all this requires a powerful machine, i do recommend at least loads of RAM 8-16Gb and a SSD.
BTW a premium solution like Avast is basic to have a safe system. Any program running in the background and sending data for analysis, like an internet security suite, is going to expose you, so usually the bigger is the company the more trustworthy (probably they are selling your data anyway) and the more anonymous. Also the more components (privacy,virus,malware,spyware,firewall,etc) it has the better as you can decrease the amount of programs from different companies and maybe have a suite, an anti-logger, anti-spy running in background. If you only have software from one company you are exposed only to that and not to several…
Conclusion: unless you have complete certainty about your OS and the machine is offline you and your information are exposed to virus, malware, Trojans… So use wisely as many solutions as you can find (using some of them portable, the ones that you run on demand for example), and be smart, expose yourself as less as possible.
I wish you all a life full of awareness, happiness, creation, evolution, and LOVE. We are part of the same system us all, our energy and our matter is constantly being mixed with the system’s energy and matter, and when we die all that energy and matter goes back to the system :)
I really hope i have a chance to win it. Good luck to everyone ! ! !
PS. Sorry i know I’m missing few things but my memory is terrible, one of the symptoms is brain inflammation…